
Microsoft security researchers revealed new details on how cyber attackers were able to exploit the 19 year old WinRar vulnerability last March using a complex attack chain and multiple code execution techniques.
The 19 year old WinRar vulnerability CVE-2018-20250 was first detected by Check Point researchers in February. Check Point warned at that time the exploit could result in code execution and allow a remote attacker to take complete control over the affected system. They added that nearly 500 million users could be at risk.
McAfee followed up with additional research in mid-March that revealed over 100 unique exploits of the WinRAR vulnerability and counting.
Rex Plantado of Microsoft’s Office 365 ATP Research Team wrote in a blog post on Wednesday that ACE files were used in a sophisticated targeted attack that “stood out because of unusual, interesting techniques.”
WinRAR uses a dll named unacev2.dll for parsing an ACE archive (a type of compressed file).
Plantado added these techniques were similar to other campaigns carried out by cyber threat group MuddyWater. Security firm Trend Micro wrote about MuddyWater’s activities dating back to 2017, to include backdoor malware tools used to target organizations in Central Asia and the Middle East.
The attack chain was illustrated in great detail on how the WinRar bug was exploited. The attack starts with a targeted spear phishing email from the “Ministry of Foreign Affairs (MFA) of the Islamic Republic of Afghanistan.”
The email includes a Word document attachment used to trigger the chain of events that eventually lead to the CVE-2018-20250 exploit as described by Microsoft in Figure 1 below.
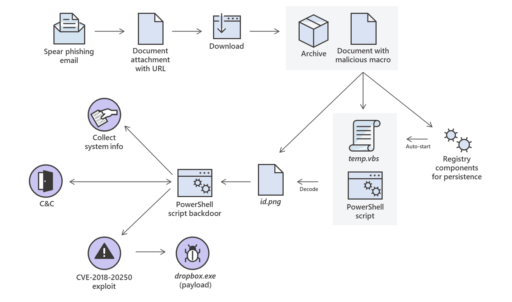
You can read the full Microsoft report for more details of the entire attack chain overview, such as malicious macro and multi-stage Powershell scripts used, as well as indicators of compromise.
Microsoft says this attack is mitigated with cyber defenses such as Office 365 ATP or Microsoft Defender ATP that can detect and block malicious behaviors across multiple stages of sophisticated attacks like the WinRar exploit.
