
Microsoft has released new Zero Trust guidance for Azure Active Directory (Azure AD). The guidance is part of a broader “Zero Trust Security Strategy” to help organizations provide more secure access to corporate resources.
Microsoft published details about the Zero Trust Security model in a video and white paper.
The Zero Trust model consists of six components all enforced via a centralized security policy: identities, devices, data, apps, infrastructure and network (see Figure 1 below).
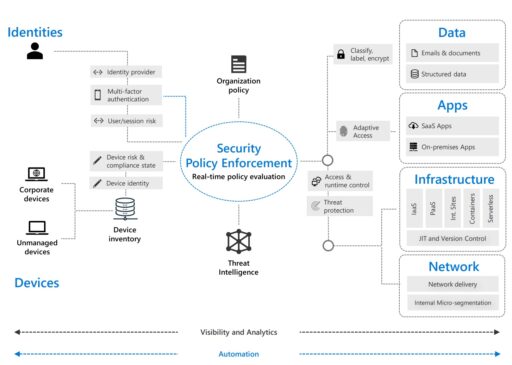
In the blog post, Microsoft describes some of the identity foundational pieces central to the Zero Trust strategy using Azure AD.
Those foundational pieces include using Azure AD to “enable strong authentication, a point of integration for device security, and the core of your user-centric policies to guarantee least-privileged access.”
For instance, Azure AD can be placed in the path of every access request to:
- Connect your organization’s users, groups and devices (such as choosing the right authentication options via Azure AD or Hybrid AD solutions).
- Integrate all your applications with Azure AD (such as single, centralized, IAM engine and SSO).
- Use Azure AD to provision or “power push” identities into apps.
- Centralized logging and monitoring of AD events.
In addition, Microsoft describes some of the key security principles of the Zero Trust strategy to include least privilege, verify explicitly, and assume breach.
Least privilege
First, the principle of least privilege means you should only give the least amount of privilege needed for the job and to the right users.
Examples of how Azure AD can be used to enforce least privilege include:
- Securing privileged access for hybrid and cloud deployments (e.g., Azure AD Privileged Identity Management, MFA, Identity Protection, dedicated admin workstations, etc.).
- Conditional access (e.g., configure your trusted IP locations in your environment).
- Restrict user consent to apps.
- Managed entitlements (such as access request, approval, and recertification process).
Verify explicity
Second, Azure AD can also enable controls to “verify the user at all times” such as:
- Multi-factor authentication (MFA).
- Azure AD Hybrid Join or Azure AD Join.
- Microsoft Intune (for managing mobile devices).
- Password-less credentials (that supports FIDO 2.0 and password-less phone sign-in).
Assume breach
Third, organizations should “assume a breach” and enable controls to help verify users, such as:
- Azure AD Password Protection (no weak passwords and prevent password attacks).
- Block legacy authentication (such as like POP, SMTP, IMAP, and MAPI) with conditional access.
- Enable identity protection.
- Restrict sessions (such as read/review vs. download files to untrusted devices).
Finally, enterprises that have purchased the Advanced Security & Information Protection (E5) license can also take advantage of additional data protections such as from phishing and zero-day malware.
Some of the E5 security controls include Conditional Access integration with Microsoft Cloud App Security (MCAS) and Microsoft Defender Advanced Threat Protection (ATP).
In conclusion, Azure AD can provide many of the foundational identity security controls for your organization and implement a successful Zero Trust strategy.
Related Articles
- NSA: Guidance to mitigate cloud vulnerabilities
- 5 Good Cybersecurity Lessons Learned From FTC Law Enforcement Actions
- Top 3 AWS security configuration mistakes
- Office 365 third-party risks and configuration guidance
