
Cybersecurity criminals are continuing to change threat tactics by leveraging more fileless malware and duel-use tools to attack organizations.
In a recent report, Cisco leverages MITRE ATT&CK tactics to help outline trends in the threat landscape specifically for endpoint security.
By detecting suspicious behaviors observed on endpoints over the first half of 2020, Cisco looked for patterns related to malicious activity.
Cisco focused on Critical threat severity vulnerabilities that are “arguably the most destructive, requiring immediate attention if seen.”
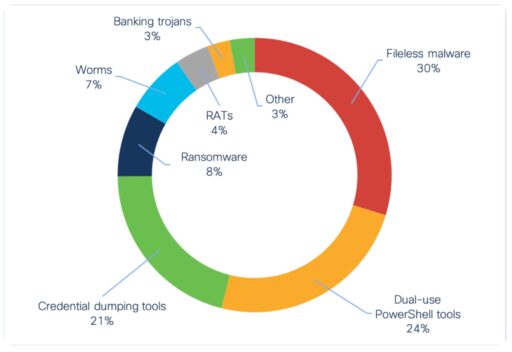
The report highlights the top three endpoint threats as fileless malware, dual use tools and credential dumping tools (a subset of dual use tools) as highlighted in Figure 1.
1) Fileless malware
According to the Cisco report, fileless malware is the most common endpoint threat and makes up 30 percent of overall indicators of compromise (IoC).
“These IoCs indicate the presence of fileless threats—malicious code that runs in memory after initial infection, rather than through files stored on the hard drive,” Cisco explained.
Examples of fileless malware threats include Kovter, Poweliks, Divergent and LemonDuck.
Readers may recall last year when attackers used a fileless malware Divergent to generate revenue via click-fraud. Divergent further used NodeJS and a WinDivert utlility to facilitate the malware attack.
The researchers also found Divergent to be similar to Kovter, another malware used for click-fraud.
2) Dual-use tools
According to Cisco, the second most popular endpoint threat (or 24% of IoCs) is dual use tools. For example, actors often use PowerShell Empire, CobaltStrike, Powersploit and Metasploit for exploitation and post-exploitation tasks.
Although many organizations use these tools for penetration tasks and to find vulnerabilities, cyber criminals also frequently use them for malicious activities.
Just last month, security experts warned that BeagleBoyz cybercriminals as part of “FASTCash 2.0” campaign had been abusing PowerShell and VBScripts to speed up operational tasks in order to compromise systems and bypass monitoring mechanisms.
In addition, Check Point researchers also recently spotted a sharp increase in Emotet botnet activity. Actors leveraged Powershell scripts to download the malware from remote sites as part of an effort to spread spam campaigns and steal banking credentials.
Last November, the BlueKeep module used in the Metasploit penetration testing framework was published. Soon afterwards, Microsoft discovered some honeypot systems were crashing after being attacked by BlueKeep exploit modules.
3) Credential Dumping tools
Coming in third place is Credential Dumping tools (or 21% of IoCs), a category of dual-use tools.
According to MITRE ATT&CK sub-techniques, OS Credential Dumping is a process where actors dump credentials to gain access to account login and passwords (usually in the form of a hash or clear text passwords). The criminals can then use the stolen credentials to move laterally and access more restricted information.
According to Cisco, Mimikatz was the most commonly observed tool used in the first half of the year. Cisco’s Endpoint Security solutions was able to spot credential dumping from memory.
Last August, Microsoft Threat Intelligence Center (MSTIC) observed GALLIUM activity targeting unpatched web servers with WildFly/JBoss vulnerabilities and use Mimikatz to dump credentials.
“Once persistence is established in a network, GALLIUM uses common techniques and tools like Mimikatz to obtain credentials that allows for lateral movement across the target network. Within compromised networks, GALLIUM makes no attempt to obfuscate their intent and are known to use common versions of malware and publicly available toolkits with small modifications,” Microsoft explained in a blog post.
MITRE ATT&CK tactics
Cisco also explained how they use the MITRE ATT&CK framework to help categorize the different IoCs. For example, a single IoC (such as PowerShell Empire) can leverage three different tactics: Defense Evasion, Execution and Credential Access.
All told, Cisco reported Defense Evasion made up over half (57%) of all IoCs. Execution came in at 41% and Persitance a distance third at 12% of all IoCs.
Cisco stated the results were not all that surprising given “avoiding detection is a key component of most modern attacks.”
However, when looking at Critical severity threats, Execution jumps up to 55% and Defense Evasion falls to 45% of all IoCs.
Mitigations
Cisco also provided a few good mitigations to guard against these endpoint threats and tactics.
For example, organizations can limit execution of unknown files, such as use group policies and/or “allow lists” for applications that are allowed to run on endpoints in their environment.
In addition, enterprises should monitor processes, registry and connections between endpoints.
“Registry modification and process injection are two primary techniques used by fileless malware to hide its activity,” Cisco explained.
Furthermore, unusual connections between different endpoints could be a sign that bad actors are attempting to move laterally across your network.
Related Articles
- 2020 Threat Landscape Report reveals new themes and evolving threats
- Divergent “fileless” NodeJS malware used for click-fraud
- BeagleBoyz cybercriminals launch “FASTCash 2.0” to rob banks
- Security experts see sharp increase in the Emotet botnet activity
- Microsoft warns more BlueKeep attacks to come
- GALLIUM targets global telecom providers
