
Microsoft has sounded the alarm on a widespread Adrozek malware campaign that targeted thousands of systems to hijack browsers, inject ads on search results and even steal passwords.
According to the Microsoft report, the cyber campaign likely started around May 2020 and picked up steam until August 2020, when up to 30,000 devices per day were attacked at its peak.
Affected browsers include Microsoft Edge, Google Chrome, Yandex Browser and Mozilla Firefox.
“Adrozek adds browser extensions, modifies a specific DLL per target browser, and changes browser settings to insert additional, unauthorized ads into web pages, often on top of legitimate ads from search engines,” Microsoft explained in the blog post on Thursday.
As a result, users could inadvertently click on malware-inserted ads while searching for keywords, which then lead to affiliated pages used by bad actors to earn money.
Attacker Infrastructure
Microsoft observed a significant “far-reaching campaign” with an “expansive, dynamic attacker infrastructure.”
Moreover, Microsoft tracked hundreds of thousands of encounters around the globe involving Adrozek malware from May to September 2020. Most of these were spotted in Europe, South Asia and Southeast Asia.
“We tracked 159 unique domains, each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique, polymorphic malware samples on average,” Microsoft added.
Malware installation
According to Microsoft, Adrozek uses the dynamic infrastructure to distribute hundreds of thousands of unique Adrozek installer samples that are “heavily obfuscated.” Each sample also uses a unique filename with the format ‘setup__.exe’.
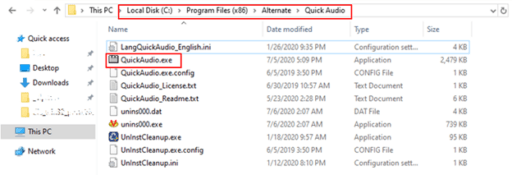
The installer then drops the malware via an .exe file with random file name in the %temp% folder. The files are named to look like legitimate audio-related software and can also be found in Settings>Apps & features (see Figure 1).
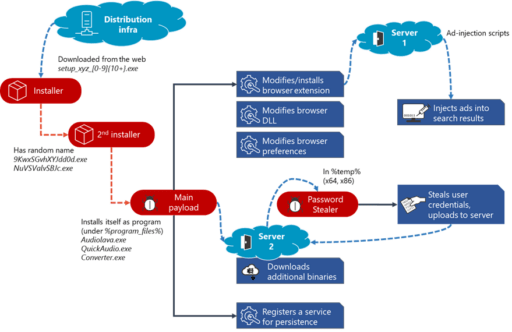
Microsoft summarizes the entire Adrozek attack chain below in Figure 2.
Browser hijacks
Adrozek can also make multiple changes to the browser settings and components. As a consequence, the malware can leverage these changes to inject ads into search engine result pages.
For example, the malware can modify one of Google Chrome’s browser default extensions called “Chrome Media Router.” Other extensions have also been used.
For Microsoft Edge and Yandex Browser, the malware can use IDs of legitimate extensions (e.g., “Radioplayer”) to disguise as a legitimate program.
In addition, Adrozek can append a folder in Firefox with a Globally Unique Identifier (GUID) to the browser extension.
“Despite targeting different extensions on each browser, the malware adds the same malicious scripts to these extensions,” Microsoft further explained.
“These malicious scripts connect to the attacker’s server to fetch additional scripts, which are responsible for injecting advertisements into search results.”
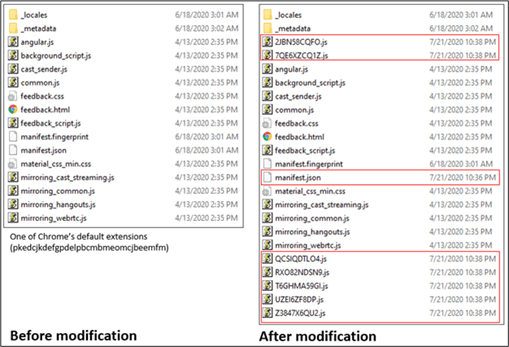
An example of this is described in Figure 3 below:
The Adrozek malware also tampers with browser DLLs in certain browsers such as Microsoft’s Edge and Chrome.
For example, the malware can modify MsEdge.dll in the Edge browser in order to turn off security controls, which is critical to detect any changes to the Secure Preferences file.
Moreover, Adrozek can also modify security settings of browsers, such as Mozilla’s Firefox, as well as Edge and Chrome.
As a result, such unauthorized changes to security permissions could allow malicious extensions to have more control over browser APIs.
To add grease to the fire, Adrozek can also add a policy to turn off security updates in compromised browsers.
Finally, readers can check out more details from Microsoft on the Adrozek threat to include how the malware gains persistence, injects ads in search results and even steals credentials after compromising systems and browsers.
