
Microsoft has published new detailed analysis of Exchange Server vulnerabilities, cybercriminal groups and post-compromise second stage attack malware. In addition, the company offered sound mitigation guidance.
Although Microsoft has confirmed they have seen a “significant decrease” in unpatched Exchange servers (now down to 92% of known Exchange IPs), the tech giant continues to work with customers and partners to mitigate the threat.
Moreover, Microsoft provided more details on the threat actors and methods used to exploit servers.
As organizations recover, Microsoft is providing new threat intelligence and guidance related to the threats but also what attackers did post-exploit of Exchange servers — to include data exfiltration, ransomware, and second-stage payload attacks.
“As organizations recover from this incident, we continue to publish guidance and share threat intelligence to help detect and evict threat actors from affected environments,” Microsoft wrote in a blog post.
Cybercriminal groups
Microsoft confirmed the first cybercriminal group that exploited the Exchange Server vulnerabilities was HAFNIUM, a state-sponsored group operating out of China.
“Attackers are known to rapidly work to reverse engineer patches and develop exploits. In the case of a remote code execution (RCE) vulnerability, the rewards are high for attackers who can gain access before an organization patches, as patching a system does not necessarily remove the access of the attacker,” Microsoft wrote.
Microsoft further described the exploit chain in the following diagram in Figure 1:
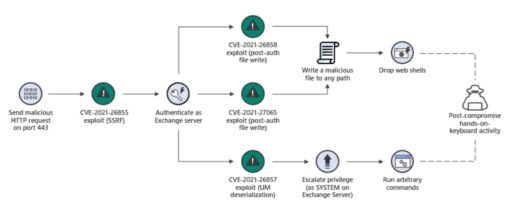
It is important to note that Microsoft warned that “many of the compromised systems have not yet received a secondary action.”
As previously mentioned, those activities could include ransomware attacks or data exfiltration. Thus, attackers could be gaining a foothold to stay undetected in order to launch future attacks.
Microsoft further described several trends used by attackers, such as:
- Web shells
- Human-operated ransomware
- Credential theft.
Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) had published reports on DearCry ransomware and China Chopper Web Shell malware linked to recent Exchange Server exploits.
Other malware used in attacks
Microsoft explained the first observed malware used in Exchange-related attacks was DoejoCrypt ransomware. The DoejoCrypt ramsomware attacks start with a variant of the Chopper web shell being deployed to compromised Exchange servers after initial compromise.
More worrisome, Microsoft warned about the dangers of how attackers could compromise service account passwords:
“The web shell writes a batch file to C:\Windows\Temp\xx.bat. Found on all systems that received the DoejoCrypt ransomware payload, this batch file performs a backup of the Security Account Manager (SAM) database and the System and Security registry hives, allowing the attackers later access to passwords of local users on the system and, more critically, in the LSA Secrets portion of the registry, where passwords for services and scheduled tasks are stored.”
Therefore, attackers look to prey on most organizations’ bad practices of not rotating service account passwords consistently and as frequent as user account passwords. As a result, those stolen credentials could be used for future second-stage attacks in the future.
Other attacks leverage the Lemon Duck cryptocurrency botnet, Pydomer ransomware (previously used in Pulse Secure VPN attacks), Maze and Egregor to name a few.
Mitigations
Finally, Microsoft provided a nice list of recommended mitigations, such as:
- Look for indicators of compromise such as web shells (regardless of patch status).
- Check out Exchange On-Premises Mitigation Tool.
- Review Local Users and Groups for unauthorized changes.
- Reset and randomize local administrator passwords (e.g., via tools like LAPS).
- Look for changes to the RDP, firewall, WMI subscriptions, and Windows Remote Management (WinRM) configuration of the system.
- Look for Security Event ID 1102 to determine if attackers cleared event logs, an activity that attackers perform with exe in an attempt to hide their tracks.
- Look for new unexpected services, scheduled tasks, and startup items (that could give clues to attacker persistence mechanisms).
- Look for unauthorized “shadow IT” tools (e.g., non-Microsoft RDP and remote access clients).
- Check mailbox-level email forwarding settings (both ForwardingAddress and ForwardingSMTPAddress attributes)
- Check other mailbox inbox rules that attackers can use to forward email externally.
- Also, check out out of the ordinary Exchange Transport rules.
Readers can check out related articles on the Exchange Server exploits and related attacks below.
Related Articles
- CISA publishes reports on DearCry ransomware and China Chopper Web Shell malware linked to Exchange Server exploits (updated)
- Cybersecurity experts warn exploits grow ten-fold after Exchange Server zero-day vulnerabilities revealed
- FBI and CISA issue urgent joint cybersecurity advisory on Exchange server hacks
- Microsoft releases emergency patches for Exchange Server RCE vulnerabilities exploited in the wild (Updated)
- Egregor Ransomware targets retail giant Cencosud, prints ransomware notes
- 2020 Threat Landscape Report reveals new themes and evolving threats
- Canon suffers ransomware attack
