
Researchers have discovered a new malware campaign that bypasses Microsoft Office malware-protections to deliver a new variant of the Zloader trojan.
Zloader is a banking trojan designed to steal passwords and personal data from users of targeted financial firms.
According to McAfee, the new obfuscation technique downloads and executes a malicious DLL aka “Zloader,” without any malicious code embedded within the attached Office document macro. As a result, the attack can stay hidden without triggering an alert.
McAfee outlined the infection chain flow in four steps as outlined in Figure 1:
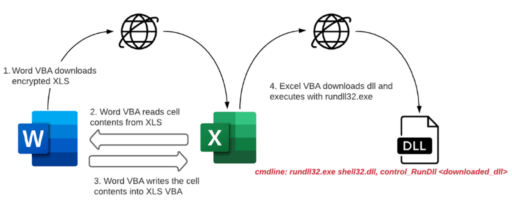
“The malware arrives through a phishing email containing a Microsoft Word document as an attachment. When the document is opened and macros are enabled, the Word document, in turn, downloads and opens another password-protected Microsoft Excel document,” McAfee wrote in the blog post.
After the Excel (XLS) file is downloaded (1), the Word Visual Basic for Applications (VBA) then reads the cell contents from the XLS file and creates a new macro (2). Then, the same XLS file writes the cell contents to the XLS VBA macros as functions (3).
As a result, the Excel VBA then downloads the Zloader payload and executes via rundll32.exe (4).
Moreover, the Command line parameter used in the attack is: Rundll32.exe shell32.dll,Control_RunDLL “<path downloaded dll>”.
In short, this means the function invokes control.exe (control panel) with the path to the malicious DLL, thereby allowing control.exe to execute the Zloader trojan.
Finally, McAfee warns attackers are evolving their techniques and obfuscation by creating agents like this to dynamically download payloads. Furthermore, actors may also use “living off the land” techniques and tools to download payloads, such as the sLoad trojan that used Windows BITS to steal data from victims last year.
Organizations and users are highly advised to disable macros in Microsoft Office applications and only enable them when documents are sent from trusted sources.
