Sandworm threat actors, also known as Voodoo Bear, are now using a new malware dubbed Cyclops Blink, a replacement for VPNFilter malware, to target small office/home office (SOHO) routers and network attached storage (NAS) devices.
Cyber experts from the United Kingdom’s National Cyber Security Centre (NCSC), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) in the U.S. issued a joint alert on the Cyclops Blink threat on February 23, 2022.
According to the alert, Cyclops Blink appears to be a replacement framework for the VPNFilter malware that was first exposed in 2018 and used to exploit SOHO and NAS devices.
In May 2018, Cisco’s Talos security group issued research reports on the then new advanced malware system dubbed VPNFilter that had compromised nearly 500,000 networking devices worldwide.
Cisco confirmed the malware code overlapped with versions of BlackEnergy malware, which was responsible for large scale targeted attacks on devices in the Ukraine.
Cyclops Blink
According to an NCSC report, Cyclops Blink is a malicious Linux ELF executable, compiled for the 32-bit PowerPC (big-endian) architecture. The malware has been associated with a large-scale botnet targeting SOHO network devices.
Moreover, the actors likely have taken advantage of weaknesses in the firmware update process present in WatchGuard Firebox and possibly other SOHO devices.
Cyclops Blink maintains persistence throughout the legitimate device firmware process as illustrated in the NCSC Figure 1 below.
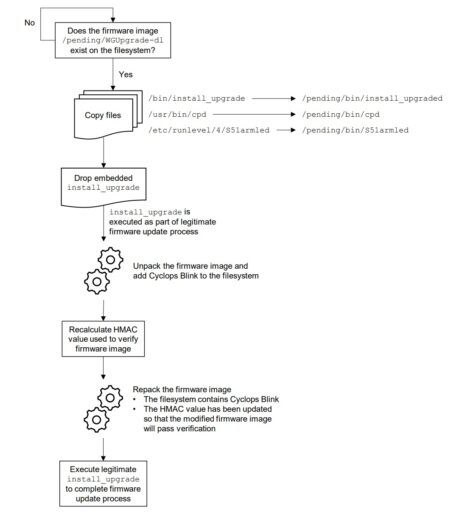
The NCSC further concluded that Cyclops Blink is a “highly sophisticated piece of malware” and likely to have infected other WatchGuard devices.
Related Articles
- VPNfilter malware targets 500K networking devices
- Ongoing VPNFilter router malware threats
- VPNFilter: New targets and developments
- Sandworm actors exploiting Exim MTA vulnerability
