Symantec security researchers have discovered a new stealth malware dubbed “Daxin” they say is the most “advanced piece of malware” linked to Chinese threat actors and is designed to target hardened networks.
Broadcom’s Symantec Threat Hunter team issued a new research report on Daxin malware that threat actors are using as part of a long-term Chinese-linked espionage campaign targeting entities in governments and critical infrastructure.
As member of the Joint Cyber Defense Collaborative (JCDC), the Symantec researchers worked with the Cybersecurity and Infrastructure Security Agency (CISA) to engage with foreign governments to detect and remediate Daxin malware.
“There is strong evidence to suggest the malware, Backdoor.Daxin, which allows the attacker to perform various communications and data-gathering operations on the infected computer, has been used as recently as November 2021 by attackers linked to China. Most of the targets appear to be organizations and governments of strategic interest to China. In addition, other tools associated with Chinese espionage actors were found on some of the same computers where Daxin was deployed,” Symantec wrote in a recent blog post.
According to the report, Daxin comes in the form of a Windows kernel driver and is extremely stealthy in nature with advanced communications features.
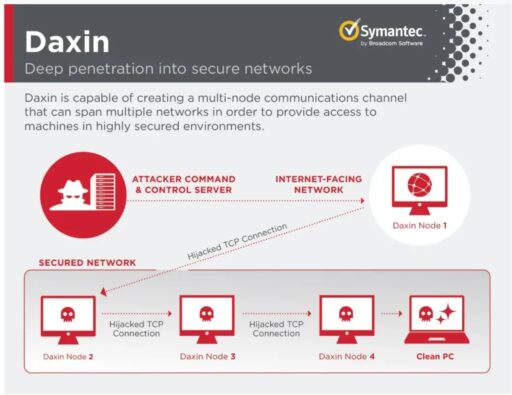
“Specifically, the malware avoids starting its own network services. Instead, it can abuse any legitimate services already running on the infected computers,” Symantec warned.
Moreover, Daxin functions as a backdoor to allow an attacker to run multiple operations on compromised systems, such as reading and writing arbitrary files. The malware can also monitor for incoming TCP traffic for certain patterns and then disconnect and hijack the connection after certain patterns are detected.
The stealthy behavior is illustrated by Symantec in Figure A below.
Finally, Daxin was most recently spotted in attacks in November 2021, but earlier samples go back to 2013, when these attackers were likely well established.

