Researchers have discovered cybercriminal group TeamTNT leaking credentials from two of their attacker-controlled accounts via exposed Docker REST APIs.
Based on a potential attack scenario, the researchers from Trend Micro setup a honeypot to show a potential attack scenario involving container registry leaks and docker-abuse malware.
“Our honeypots showed threat actor TeamTNT were leaking credentials from at least two of their attacker-controlled DockerHub accounts, namely alpineos (with over 150,000 pulls) and sandeep078 (with 200 pulls). We have notified Docker about these accounts,” Trend Micro explained in a blog post.
Trend Micro monitored the TeamTNT’s malicious activities against the honeypot in mid to late 2021 and will present their findings in an upcoming 0c0n XV Hacking and Cyber Security Conference.
The security experts also found DockerHub profiles deployed malicious images that include the following malware:
- Rootkits
- Docker escape kits
- XMRig Monero miners
- Credential stealers
- Kinsing malware
- Kubernetes exploit kits.
Moreover, Trend Micro presented one attack scenario where an image pulled from DockerHub contained the Base64-encoded credentials (Figure 1):
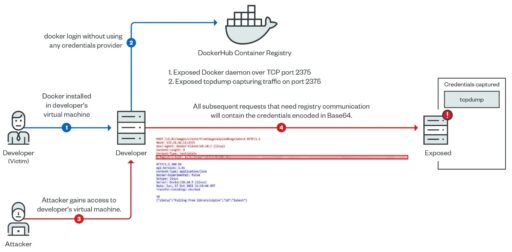
In the second scenario, an attacker’s credentials could be leaked (see Figure 2):
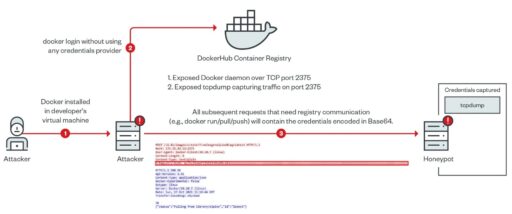
In conclusion, Trend Micro warned that cyber threat actors can exploit component misconfigurations when gaps are found.
“Organizations’ security teams need to be aware that developer security is critical considering this type of compromise around developer-centric tools like Docker have been observed being abused by threat actors,” Trend Micro added.
Related Articles
- Linux Cgroup vulnerability can cause container escape
- Siloscape: The first malware to target Windows containers
- PwnKit: “Trivially exploitable” vulnerability found in Linux Polkit’s pkexec tool
- Ubuntu 21.04 (Hirsute Hippo) end-of-life January 20, 2022
- Two Kubernetes vulnerabilities patched
- Serious open-source container vulnerability
- Misconfigured Docker containers abused to deliver cryptocurrency mining malware
- What Are Application Containers And How Do I Secure Them?
- Microsoft container tool patch

