Security researchers from Palo Alto Networks Unit 42 have discovered a Mirai botnet variant dubbed “MooBot” that targets multiple D-Link flaws and exposed networking devices running Linux.
According to Unit 42 research, MooBot is targeting these D-Link vulnerabilities:
- CVE-2015-2051: D-Link HNAP SOAPAction Header Command Execution Vulnerability
- CVE-2018-6530: D-Link SOAP Interface Remote Code Execution Vulnerability
- CVE-2022-26258: D-Link Remote Command Execution Vulnerability
- CVE-2022-28958: D-Link Remote Command Execution Vulnerability.
On September 8, the Cybersecurity and Infrastructure Security Agency (CISA) also added CVE-2018-6350, CVE-2022-26258, and CVE-2022-28958 to the Known Exploited Vulnerabilities Catalog.
Moreover, these cyberattacks are low complexity and could lead to remote code execution and critical impact to affected entities.
“If the devices are compromised, they will be fully controlled by attackers, who could utilize those devices to conduct further attacks such as distributed denial-of-service (DDoS) attacks,” Unit 42 explained in the blog post.
Unit 42 described the attack in Figure 1 below:
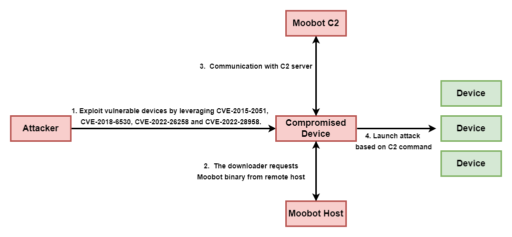
Readers can check out the full report for more details on MooBot campaign, D-Link exploit payloads, malware analysis and indicators of compromise.
Related Articles
- Threat actors exploit Spring4Shell to weaponize and execute Mirai botnet
- New Mirai variant exploits IoT devices
- New Mirai, Gafgyt IoT botnet variants target systems with Apache Struts, SonicWall vulnerability exploits
- Palo Alto Networks: Network Security Trends report highlights common RCE vulnerability exploits against web apps

